Viral News | Explore around Viral and popular News this year
Secure And Convenient Identity Management For Businesses And Individuals
Secure And Convenient Identity Management For Businesses And Individuals
Editor's Notes: "Secure And Convenient Identity Management For Businesses And Individuals" have published today date. Given the criticality of identity management in today's digital age, understanding its nuances is paramount for both businesses and individuals.
To help our readers make informed decisions about their identity management needs, we have analyzed, dug up information, and put together this comprehensive guide. We cover the key benefits, challenges and solutions associated with secure and convenient identity management, empowering you to make the right choice for your organization or personal needs.
FAQs
This section provides answers to frequently asked questions about Secure and Convenient Identity Management for Businesses and Individuals. These FAQs aim to address common concerns and misconceptions, providing clarity and insights into the subject matter.
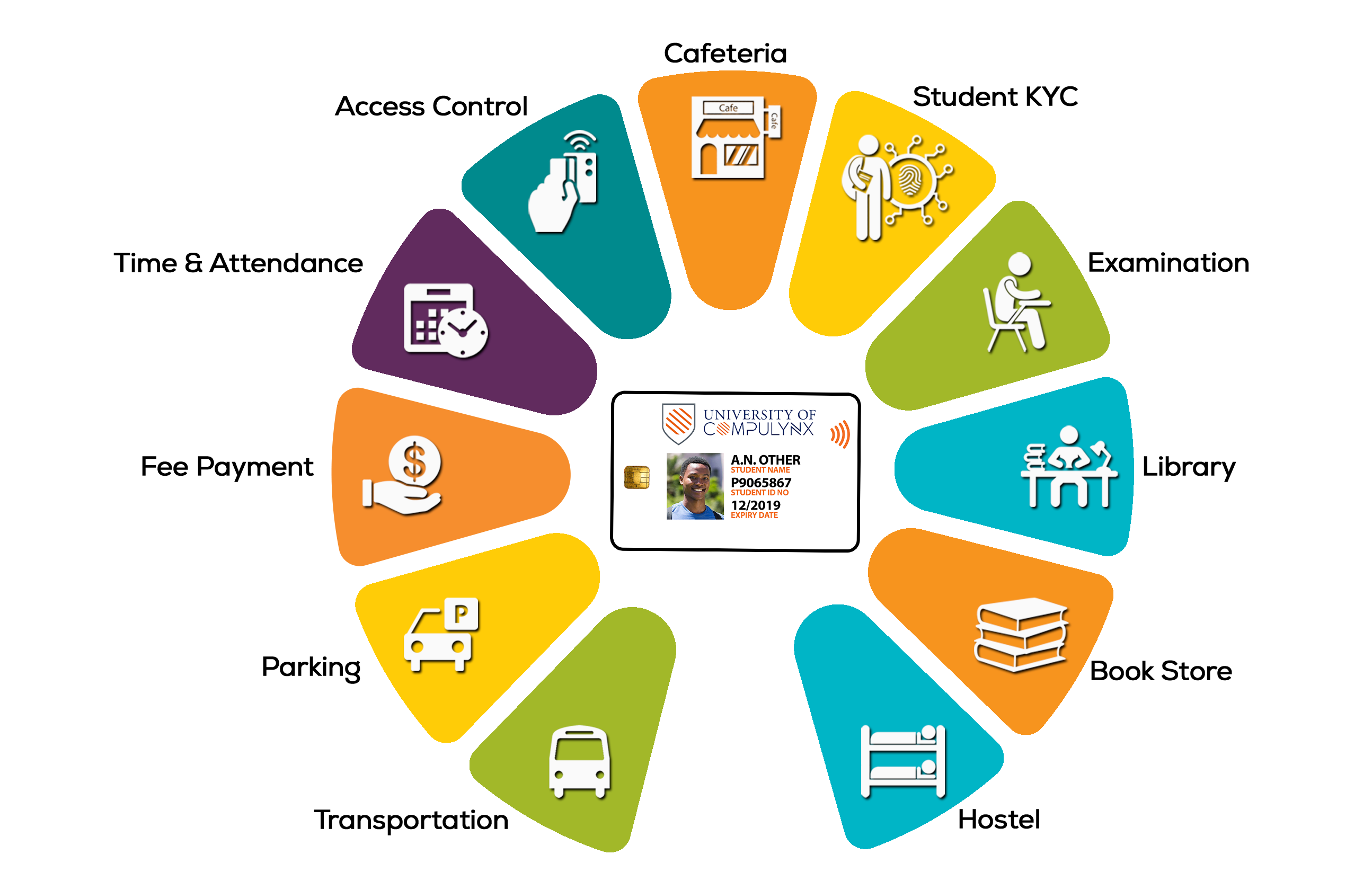
Student Identity Management | CompuLynx - Source compulynx.com
Question 1: What are the benefits of implementing identity management solutions for businesses?
Implementing identity management solutions offers numerous benefits to businesses. These include enhanced security by preventing unauthorized access to sensitive data, streamlined user experience through centralized authentication and authorization, improved compliance with regulatory requirements, and increased productivity due to simplified and automated identity management processes.
Question 2: How can identity management protect individuals from online threats?
Identity management solutions play a crucial role in safeguarding individuals from online threats. They provide strong authentication mechanisms, such as multi-factor authentication, to prevent unauthorized access to accounts and personal information. Additionally, these solutions implement real-time monitoring and anomaly detection systems to identify and respond to potential security breaches, protecting individuals from fraud, phishing, and other cyberattacks.
Question 3: What are the different types of identity management solutions available?
Identity management solutions come in various forms, each tailored to meet specific requirements. These include cloud-based identity management, on-premises identity management, and hybrid identity management. Cloud-based solutions offer flexibility and scalability, while on-premises solutions provide greater control and customization. Hybrid solutions combine both approaches, providing a balance of flexibility and control.
Question 4: How can identity management solutions help improve compliance with regulations?
Identity management solutions facilitate compliance with regulations by providing features that enable businesses to adhere to industry standards and legal requirements. These features include centralized user management, role-based access control, audit trails, and reporting capabilities. By implementing these solutions, businesses can demonstrate compliance with regulations such as GDPR, HIPAA, and PCI DSS.
Question 5: What are the key considerations when selecting an identity management solution?
When selecting an identity management solution, several key considerations come into play. These include the size and complexity of the organization, security requirements, scalability needs, budget constraints, and ease of integration with existing systems. It is crucial to evaluate these factors carefully to choose the solution that best aligns with the specific needs and objectives of the organization.
Question 6: How does identity management contribute to digital transformation initiatives?
Identity management is a fundamental aspect of digital transformation initiatives. It provides the foundation for secure and seamless access to applications and services, enabling businesses to embrace cloud computing, mobile technologies, and other emerging technologies. By implementing robust identity management solutions, organizations can securely manage user identities, protect access to sensitive data, and enhance the overall efficiency and effectiveness of their digital transformation efforts.
In conclusion, identity management solutions are indispensable for businesses and individuals to navigate the increasingly complex and interconnected digital landscape. They provide a comprehensive approach to securing identities, safeguarding data, and enhancing user experience. By understanding the benefits, types, and considerations involved in identity management, organizations and individuals can make informed decisions and implement solutions that meet their specific requirements.
For more information and insights into Secure and Convenient Identity Management for Businesses and Individuals, continue exploring our website.
Tips for Secure and Convenient Identity Management
Identity management is a critical aspect of data security and privacy. By implementing effective identity management practices, businesses and individuals can protect their sensitive information from unauthorized access. Here are some tips to help you achieve secure and convenient identity management:
Tip 1: Use Strong Passwords
Strong passwords are essential for protecting your accounts from unauthorized access. Avoid using easily guessable passwords such as your name, birthday, or common words. Instead, create passwords that are at least 12 characters long and include a combination of uppercase and lowercase letters, numbers, and symbols.
Tip 2: Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your accounts. When you log in to an account with 2FA enabled, you will be prompted to enter both your password and a code that is sent to your mobile phone or email address. This makes it much more difficult for attackers to gain access to your account, even if they have your password.
Tip 3: Use a Password Manager
Password managers are software programs that store your passwords in an encrypted format. This makes it easy to create and manage strong passwords for all of your accounts without having to remember them all. Password managers also often include features such as automatic login and password generation.
Tip 4: Be Aware of Phishing Scams
Phishing scams are emails or websites that are designed to trick you into revealing your personal information, such as your passwords or credit card numbers. These scams often look like they are from legitimate organizations, but they are actually fake. Be wary of any emails or websites that ask you to click on a link or enter your personal information. If you are unsure whether an email or website is legitimate, do not click on any links or enter any information.
Tip 5: Keep Your Software Up to Date
Software updates often include security patches that fix vulnerabilities that could be exploited by attackers to gain access to your accounts. It is important to keep your software up to date to protect your devices and data from threats.
By following these tips, you can help to secure and protect your identity online.
For more information on identity management, see: Secure And Convenient Identity Management For Businesses And Individuals.

Digital Identity Management | Gadarian Digital - Source www.gadarian.com
Secure And Convenient Identity Management For Businesses And Individuals
In today's digital landscape, secure and convenient identity management has become paramount for both businesses and individuals. This involves implementing robust mechanisms to safeguard personal and sensitive information, while also ensuring seamless access to services and resources.
- Authentication: Verifying user identities through secure protocols.
- Authorization: Determining user permissions based on access control policies.
- Data Privacy: Protecting user data from unauthorized access and breaches.
- Centralized Management: Streamlining identity management processes for efficient administration.
- User Experience: Ensuring a frictionless experience for users, minimizing access barriers.
- Regulatory Compliance: Adhering to industry standards and regulations for data protection.

The value of organisation identity - Source www.ubisecure.com
These aspects are interconnected and essential for effective identity management. By implementing robust authentication mechanisms, businesses can prevent unauthorized access to sensitive information. Centralized management enables efficient user and access management, while data privacy safeguards protect against data breaches. User experience enhancements ensure seamless access to resources, fostering productivity. Regulatory compliance ensures adherence to industry standards, protecting businesses from legal liabilities. In conclusion, secure and convenient identity management requires a comprehensive approach that encompasses these key aspects, ensuring the protection of sensitive data, seamless access to resources, and regulatory compliance.
Secure And Convenient Identity Management For Businesses And Individuals
Identity management is a critical component of security in the digital age. As businesses and individuals increasingly rely on online platforms, the need for secure and convenient ways to manage identities is paramount. Secure identity management solutions provide a range of benefits, including:

Decentralized Identity Management Risks - How SSI and DID Work - Source identitymanagementinstitute.org
Improved security: By implementing strong authentication mechanisms, such as multi-factor authentication, businesses can reduce the risk of unauthorized access to data and systems. Single sign-on (SSO) solutions also eliminate the need for users to remember multiple passwords, which reduces the likelihood of credential theft.
Enhanced convenience: Identity management solutions can streamline the authentication process, making it easier for users to access the resources they need. SSO allows users to access multiple applications and services with a single set of credentials, while password managers help users to securely store and manage their passwords. This can save time and reduce frustration for users, while also improving security.
Reduced costs: By automating the identity management process, businesses can reduce the administrative overhead associated with manual processes. SSO solutions can also reduce the number of help desk calls related to password resets, freeing up IT staff to focus on other tasks.
Improved compliance: Secure identity management solutions can help businesses comply with industry regulations and standards. These solutions can provide audit trails and reporting capabilities that demonstrate compliance with data protection and privacy laws.
Conclusion
Secure and convenient identity management is essential for businesses and individuals in the digital age. By implementing these solutions, businesses can protect their data and systems from unauthorized access while also improving the user experience for their employees and customers. Individuals can also benefit from secure identity management solutions by reducing the risk of identity theft and fraud.
As technology continues to evolve, it is likely that identity management will become even more important. New technologies, such as biometrics and blockchain, are being developed to provide even more secure and convenient ways to manage identities. Businesses and individuals who stay ahead of the curve on these technologies will be better positioned to succeed in the digital age.